- लिंक पाएं
- X
- ईमेल
- दूसरे ऐप
The Android story told through one hilarious Facebook timeline
It all started with
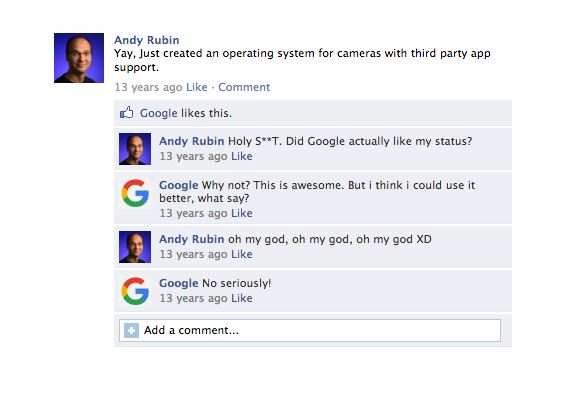
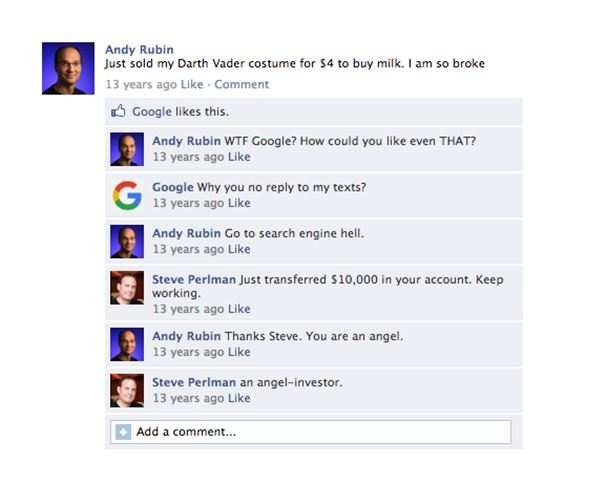
Pretty soon Andy Rubin went broke trying to make ends meet, only to be saved by Steve Perlman who helped him stay afloat.
Along came Google,
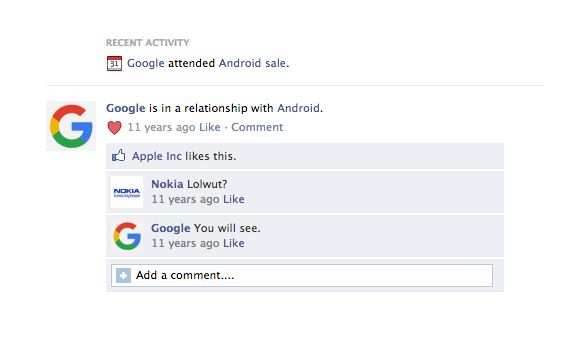
Google had to partner with
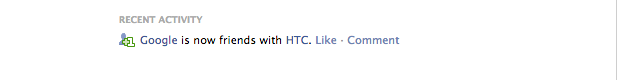
The HTC dream was released on 20th October 2008.
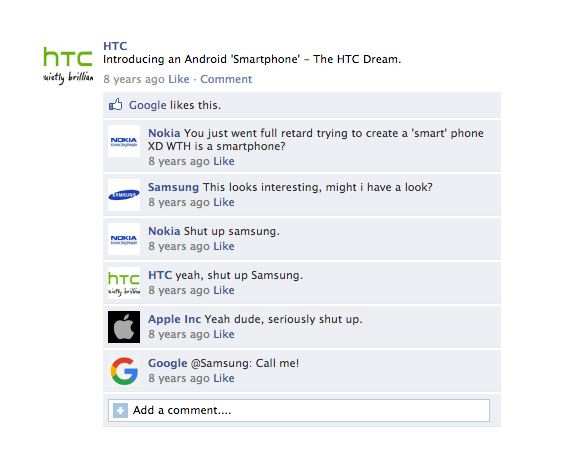
Even though Google faced initial failures with Nexus. More OEMs jumped in on the Android smartphone bandwagon.
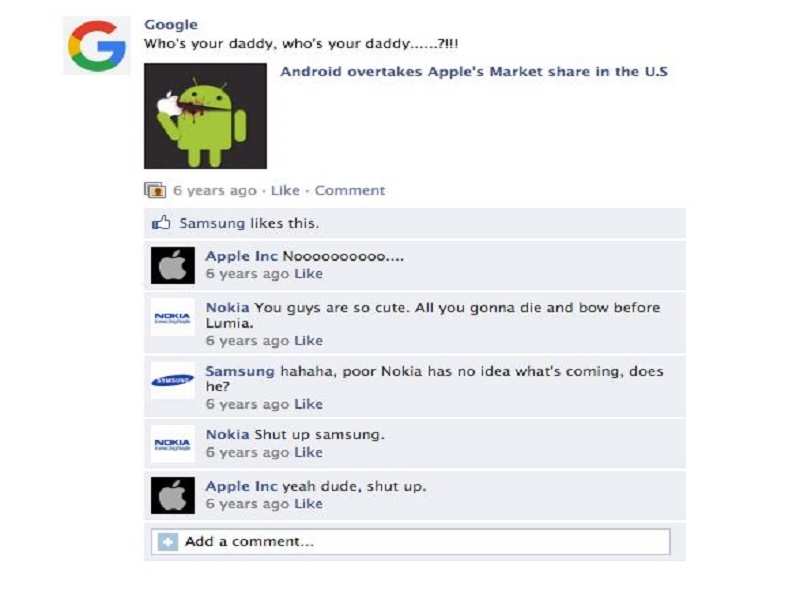
Due to
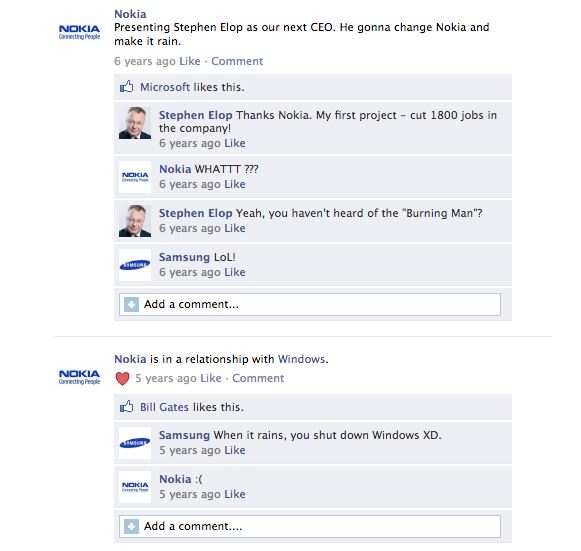
Samsung kept benefitting from the Android ecosystem to become one of the largest OEMs in the world.
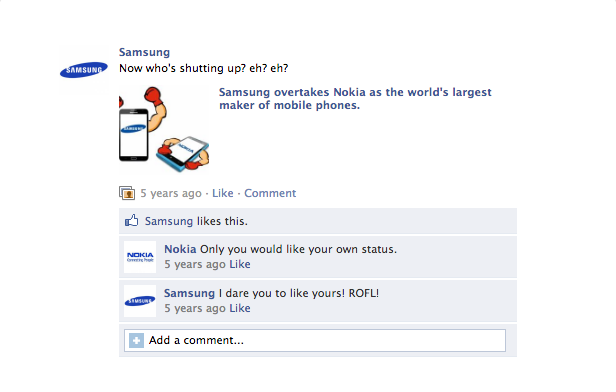
Google kept contributing heavily to the Android platform. Google initially bought
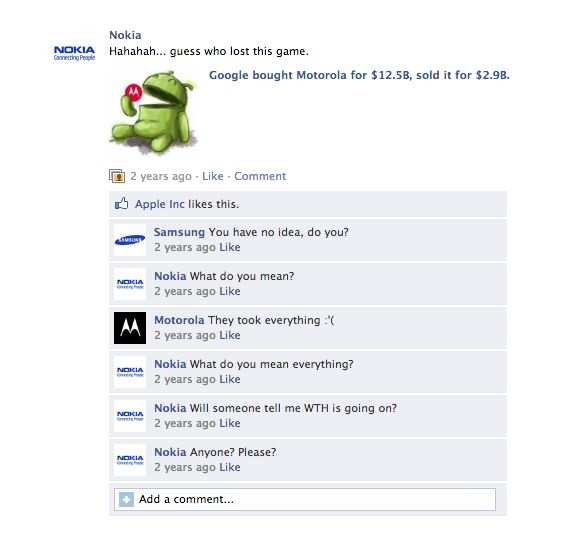
Owing to the continuous rise of Android that took over above 86% of the smartphone market. Google took another turn.
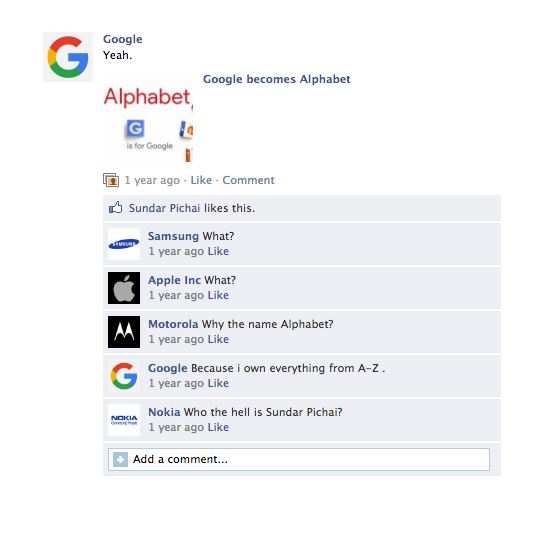
So huge is the bet on Android's future that early this year, Alphabet overtook
NEXT STORY
Russia's capital now has its own version of Pokemon Go - with historical figures

CONTINUE READING
"Know. Moscow. Photo" operates in a similar fashion to Pokemon Go, allowing users to capture virtualcharacters in real-life locations with their smartphone cameras. However, instead of hunting Pokemon, users search for and capture important Russian historical figures, according to Moscow's Department of Information Technologies.
"The goal of the app is to attract attention to Moscow's rich cultural heritage using fashionable augmented reality technology, as well as give Muscovites a reason to walk around more," the city government said, according to The Guardian.
Virtual doubles of historical figures who are already wandering through the capital include Russian tsars Ivan the Terrible and Peter the Great, first man in space Yuri Gagarin, Soviet rock legend Viktor Tsoi, the composer Pyotr Tchaikovsky, poet Alexander Pushkin, and Napoleon Bonaparte, who invaded Moscow in 1812, according to the Moscow government.
Unlike Pokemon Go, where Pokemon populate semi-randomly on the map, the historical figures in "Know. Moscow. Photo" appear in specific places in Moscow based on their life stories. For example, Tsoi can be found near a graffiti-covered wall bearing his name on the Arbat Street. The landmark is dedicated to Tsoi and is frequently visited by fans.
Once the full version launches in August, characters will begin appearing in multiple addresses or may move around, forcing users to search for him or her, according to the Moscow mayor's office.
Many Russian government members have criticized the app however.
Ruling party MP Yevgeny Fyodorovaccused the app's developers of using it to cause "mass disturbances" and to destabilize Russia before parliamentary elections in September in an interview with Russian news website National News Service. The Communist MP Vadim Solovyov even called for banning the game, comparing it to drugs and gambling, according to MSK Agency, a Moscow-based news service.
"There's the feeling that the devil came through this mechanism and is trying to simply tear us apart spiritually from within," senator Frants Klintsevich toldthe state news agency Russia Today.
NOW WATCH: You can print your photos as pancakes now
NEXT STORY
We just got another peek at what the ultra secretive Magic Leap headset can do

CONTINUE READING
Magic Leap has unveiled another brief demo of its forthcoming augmented reality technology, this time showcasing how online shopping might work on the device.
As noted by Road to VR, Magic Leap CMO Brian Wallace introduced the 70-second video at an Alibaba-sponsored event in China last week. Alibaba previously made significant investments in the Florida-based startup.
The clip itself is mostly in Chinese, but shows a person using Magic Leap to browse through a virtual selection of accessories for a small desk. After selecting a product, the person can see its rating and pricing details, and preview how it'd look in the real world.
You should really see this demo for yourself.
In many ways, it's similar to what Lenovo has shown with its Phab 2 Pro phone, which uses Google's "Tango" AR platform. Instead of using your phone to map out an area, though, you use a device that's already over your eyes.
Magic Leap confirmed the demo to Tech Insider, saying it doesn't specifically indicate what shopping through Alibaba will look like on the device. Instead, it's meant to be a general look at one capability Magic Leap owners will have in the future. In other words, it's still swearing to secrecy.
That said, last month Magic Leap CEO Rony Abovitz noted that the company is "turning on the first production line in [its] factory throughout this summer." At the same time, it announced a partnership with LucasFilm, and showcased a demo featuring Star Wars characters. The video above might not be as exciting as that, but it does give us another idea of what we can expect - in some form or another.
NEXT STORY
This is How Hackers attacked WikiLeaks, Visa and Paypal

CONTINUE READING
What are DoS and DDoS Attacks?
I can't tell you who attacked Wiki leaks,PayPal , Visa or any other company out of three quarters companies that faced this brutal Distributed Denial of Service attack (DDoS). But let me tell you they were as easy as putting a cherry on top of a cake. Just Google if you wish to see how brutal they were. WikiLeaks was buried under 10 gb/sec data load on the website, just imagine the intensity of attacks on corporations. To a fact, Anonymous (Hacktivist group) used this in Arab spring.
Who's behind these attacks?
Individuals tend to consider DDoS destroys by sticking network bandwidth with futile traffic. While that is unquestionably one sort of DDoS attack, others work by eating up server resources. That implies it's workable for a fruitful DDoS assault to be made regardless of the amount of bandwidth you have in light of the fact that it attacks your servers' resources. To truly ensure a network against attacks, both your Internet connection and your servers need guards.
What is DoS (Denial of Service) Attack?
In a denial-of-service (DoS) attack, an attacker endeavours to keep legitimate users from getting to data or services. By focusing on your PC and its network connection, or the PCs and network of the destinations you are attempting to utilize, an attacker might have the capacity to keep you from getting to email, sites, online records, or different services that depend on the affected system.
The most widely recognized and evident kind of DoS attack happens when an attacker "surges" a network with data. When you write a URL for a specific site into your program, you are sending a request to that site's server to see the page. The server can just process a specific number of requests, so if an attacker over-burdens the server with requests, it won't be able to complete your request. While DDoS is an attack which is performed by various compromised systems that target the same victim. It surges the network with data packets.
Most common types
Smurf: This sort of attack uses large number of Internet Control Message Protocol (ICMP) pings to focus at an Internet Broadcast Address. The answer IP location is ridiculed to that of the expected casualty. Every answer is sent to the casualty rather than the IP utilized for the pings. Since a single Internet Broadcast Address cannot surpass 255 hosts, a smurf attack increases the ping 255 times. The impact of this is slowing the network to a point where it is impossible to use it.
How does it work?
1. The hacker identifies victim's IP address
2. Hacker recognizes a mediator site that will intensify the attack
3. The hosts on the victim's system reacts to the ICMP requests
4. This makes a lot of movement on the victim's system, bringing about consumption of bandwidth and at last creating the victim's server to crash.
Ping of Death: POD is an old denial of service attack that was successful some time back, but is not even a bit dangerous any more. Ping of Death has additionally been called Teardrop, and a couple of different names.
Inside the IP protocol there are maximum byte allowances for packets (data) sent between two machines. The maximum allowance under IPv4 is 65,535 bytes. At the point when a substantial packet is sent it is isolated over different IP packets. Since the sent information packages are bigger than what the server can deal with, the server can solidify, reboot, or crash.
SYN Flood
SYN is short form for Synchronize. SYN Attack is a kind of Distributed Denial of Service (DDoS) attack that endeavours part of the ordinary TCP three-way handshake to consume resources on the targeted server and render it unresponsive.
Basically, with SYN surge DDoS, the hacker sends TCP connection requests faster than the targeted machine can prepare them, bringing about network immersion.
Security patches for operating systems, router configuration, firewalls and intrusion detection systems can be used to protect against denial of service attacks.
I can't tell you who attacked Wiki leaks,
Who's behind these attacks?
Individuals tend to consider DDoS destroys by sticking network bandwidth with futile traffic. While that is unquestionably one sort of DDoS attack, others work by eating up server resources. That implies it's workable for a fruitful DDoS assault to be made regardless of the amount of bandwidth you have in light of the fact that it attacks your servers' resources. To truly ensure a network against attacks, both your Internet connection and your servers need guards.
What is DoS (Denial of Service) Attack?
In a denial-of-service (DoS) attack, an attacker endeavours to keep legitimate users from getting to data or services. By focusing on your PC and its network connection, or the PCs and network of the destinations you are attempting to utilize, an attacker might have the capacity to keep you from getting to email, sites, online records, or different services that depend on the affected system.
The most widely recognized and evident kind of DoS attack happens when an attacker "surges" a network with data. When you write a URL for a specific site into your program, you are sending a request to that site's server to see the page. The server can just process a specific number of requests, so if an attacker over-burdens the server with requests, it won't be able to complete your request. While DDoS is an attack which is performed by various compromised systems that target the same victim. It surges the network with data packets.
Most common types
Smurf: This sort of attack uses large number of Internet Control Message Protocol (ICMP) pings to focus at an Internet Broadcast Address. The answer IP location is ridiculed to that of the expected casualty. Every answer is sent to the casualty rather than the IP utilized for the pings. Since a single Internet Broadcast Address cannot surpass 255 hosts, a smurf attack increases the ping 255 times. The impact of this is slowing the network to a point where it is impossible to use it.
How does it work?
1. The hacker identifies victim's IP address
2. Hacker recognizes a mediator site that will intensify the attack
3. The hosts on the victim's system reacts to the ICMP requests
4. This makes a lot of movement on the victim's system, bringing about consumption of bandwidth and at last creating the victim's server to crash.
Ping of Death: POD is an old denial of service attack that was successful some time back, but is not even a bit dangerous any more. Ping of Death has additionally been called Teardrop, and a couple of different names.
Inside the IP protocol there are maximum byte allowances for packets (data) sent between two machines. The maximum allowance under IPv4 is 65,535 bytes. At the point when a substantial packet is sent it is isolated over different IP packets. Since the sent information packages are bigger than what the server can deal with, the server can solidify, reboot, or crash.
SYN Flood
SYN is short form for Synchronize. SYN Attack is a kind of Distributed Denial of Service (DDoS) attack that endeavours part of the ordinary TCP three-way handshake to consume resources on the targeted server and render it unresponsive.
Basically, with SYN surge DDoS, the hacker sends TCP connection requests faster than the targeted machine can prepare them, bringing about network immersion.
Security patches for operating systems, router configuration, firewalls and intrusion detection systems can be used to protect against denial of service attacks.
NEXT STORY
After it went viral on iOS, Prisma now on Android

CONTINUE READING
Our Facebook walls have been filled with
Don't mistake Prisma with your ordinary filters as it does much more than simply overlaying images with different kinds of filters, it uses artificial intelligence algorithms to generate its images. Prisma reconstructs the image from scratch by making intelligent design choices. Yes, AI is involved, you have to try it to believe it. While it takes a little longer than applying a filter as it is rebuilding the image from scratch but once you give it a go you will create art.
On iOS Prisma has over 10.6 million installs, Android is buzzing and it's going to be very easy to get user attention as Android users were already clamoring to use its capabilities on their devices. The big challenge for Prisma now is to take on the Android influx without succumbing to the pressures of its popularity.
Prisma is a free app and it effortlessly integrates with social media like Facebook,
NEXT STORY
The 10 most futuristic concept cars in the world
CONTINUE READING
Cars of the future could be more high-tech than most homes.
That's at least what we're gathering from the futuristic concept cars automakers have been building.
We rounded up the most tech-savvy cars we could find and what it means for the future of driving.
Comments ()

Characters Remaining: 3000
Sort By:

NEXT STORY
This $99 device can turn your smartphone into a full-fledged laptop

CONTINUE READING
Basically, they've tried really hard to have you buy a smartphone (the computer you carry in your pocket) that can also be your laptop (the computer you use at home).
Microsoft has been the most visible proponent of this idea in recent months; its Continuum feature allows Windows Phones to run a lightweight version of Windows 10 when plugged into a display dock. The problem, in a nutshell, is that nobody buys Windows Phones.
Before Microsoft, there was Ubuntu. It's long struggled to gain traction with similar promises, dating all the way back to its failed Edge project in 2013.
Before that, there was Motorola. Its Atrix phone worked the same way, but its laptop dock cost $500, the software you used with it was half-baked, and the phone was only "strong" by 2011's standards. Again, few people cared.
Still, the dream hasn't died. The latest group to give it a try is Andromium, a startup headed by alumni of Google and Y Combinator. Its new Kickstarter project, the Superbook, essentially revamps the Atrix concept and applies it to various Android phones.
How it works
At its core, the Superbook is just a laptop shell. It's got an 11.6-inch display with a 1366x768 resolution, a QWERTY keyboard with Android-specific keys, a multi-touch trackpad, and a battery that Andromium rates at eight or so hours of use. (Though that'll move closer to 10 hours if Andromium reaches $500,000 in funding, which currently looks likely.) In a recent Reddit AMA, the company said the device is composed of soft plastic.
In other words, it's small and basic. It makes up for that by being cheap - it starts at $99 through Kickstarter, and the company expects it to start in the $129 range if and when it hits retailers. (If the campaign hits $1 million, the company plans to offer a slightly more expensive 1080p display option as well.)
To power it, you activate the Andromium OS app - which is available in beta form in the Google Play Store - on your phone, then plug it into the shell over microUSB or USB-C. You're not limited to any particular model, but the company says the phone should have at least 1.5GB of RAM, a dual-core chip, and Android 5.0 or higher. (It also has to support the USB-OTG standard, but that shouldn't be an issue for the vast majority of devices.)
The idea, as it's always been, is to leverage your phone's power with a laptop's form factor. In Andromium's eyes, having buying a new phone then becomes akin to buying a new laptop.
Familiar questions remain
Now, that probably won't hold true for everyone. A cheaper phone won't be as smooth as a pricier one. Plenty of Chromebooks are affordable and perfectly capable. And while your phone is a tiny computer, it's not a tinylaptop - much of the Superbook's success will come down to how well Andromium OS turns Android into competent desktop software.
That said, it does seem to have the basics down - a browser, a file manager, a taskbar, a launcher, some level of multitasking, etc. - and as we've seen on Chrome OS, Android itself has plenty of apps that translate well enough to desktops. You can watch videos on YouTube, write documents with Microsoft Word, and play a bunch of games.
Andromium says it'll open its SDK so developers can tailor their apps for Andromium, too, though how much support that gets remains to be seen.
In any case, the campaign has raised more than $400,000 in a couple days of funding, way past its initial target. While the usual risk with crowdfunding projects remain, Andromium says its prototypes are finished, and that it hopes to ship the Superbook to backers by February 2017.
Either way, given how strong today's smartphones have become, the time might finally be right to make this nerd fantasy a reality. Again.
NEXT STORY
Xiaomi's ₹1 flash sale gives away one million worth merchandise to a total of 330 winners

CONTINUE READING
To celebrate its 2 nd anniversary in India,
Here's what happened
On the first day of ₹1 flash sale, Xiaomi sold 10 units of one of its most popular flagship phones,
On the second day 10 Redmi Note 3 that usually costs Rs. 10,198 were sold for 1 to 10 super quick lucky winners and some had to make do with Mi Band 1A that's worth Rs.1099, not at all a bad deal for Re.1.
On the third day 10 flash sale pros got the latest phone from Xiaomi,
Well, where there were very few lucky winners many were left clicking disappointed. All we can say is better luck next time .
NEXT STORY
Here’s how you can score Xiaomi’s ₹ 1 Flash Deal

CONTINUE READING
For many of you who missed the chance to grab that awesome Re. 1 deal from
Here's Xiaomi's words of wisdom for the flash sale
Step 0
Always make sure you are logged in to your mi.com account way before the sales start!
Step 1
To sign up, click the 'Share to Register' button and spread the news on your Facebook feed.
If you aren't registered when the ₹ 1 Flash Deal starts, you'll have to spend extra time registering and you'll miss out because these flash deals will go out in a nanosecond. (That's why FLASH deal, right!)
Step 2
Once you have shared you will see the 'Share to register' button change to 'Coming soon'.
This means you are eligible to buy when the flash deal starts at 2pm. You will only have to 'Share' the news to your Facebook once, to be eligible for all ₹1 Flash Deal happening across the 3 days.
Step 3
Once the sale starts the 'Coming soon' button will change to 'Buy now'
You can keep track of the time via the countdown timer on the left. #Protip: always be there earlier than the actual sales time, because these things go out in a FLASH.
Step 4
There are 2 flash deals going on one for a Mi phone, another for a Mi Accessory. There will be a 'Buy now' button below each product, and clicking one button does not mean you are buying both products.
Step 5
If you managed to be the lucky one who has grabbed a Mi product at ₹1, your name will be added to the winners list at the top of this thread. The Mi product will also be added to your cart. Make sure you place your order, and pay within 2 hours or your hard earned ₹1 Flash Deal will be removed from your cart.
Good Luck!
NEXT STORY
Reliance Jio could be the biggest 4G player in the country even before its commercial launch, coming this Diwali

CONTINUE READING
Commercial launch of billionaire
Capacity
Reliance Jio has been clear that when they come it's going to be with a capacity that can allow fastest internet access to subscribers. CLSA said "Jio's subscribers are already using an average of 26 GB a month, Jio's monthly data traffic is nearing 39 million GB. Jio's network may already be handling the second- highest data traffic". And even with major rise in traffic on Jio network, CLSA's tests reveal no notable drop in user experience. CLSA note says Jio's network can easily handle usage of 5 GB per month data each by over 100 million subscribers. And that may be Jio's core strategy too.
Pricing
While it's clear that when the Jio commercial launch happens, it's going to be one of the biggest tariff wars in the industry as Reliance Jio is expected to come with never seen before offers. So far Jio is offering 3 month complementary services with their LYF handsets and they have recently dropped the entry -level price of LYF's 4G phones. Jio has also extended the offer with premium
http://www.businessinsider.in/Android-story-told-through-Facebook-updates/articleshow/53393256.cms
- लिंक पाएं
- X
- ईमेल
- दूसरे ऐप







































Comments (0)